
In earlier years, everyone depended on CyberSOC (including firewalls, WAF, SIEM, etc.) and the priority in building the SOC provided security, and the CIA was maintained.
However, later the emergence of the attacks and the threat actors becomes more challenging and the existing SOC will not be able to provide better security over the CIA.
There are many reasons for the failure of the existing SOC, where it only depends on the SIEM.
Many organizations believe integrating all the security devices like Firewalls, Routers, AV, and DB solutions in SIEM and correlating the use cases will provide them 100% security over the CIA of the data.
However, it all fails, since the APT emerges.
APT attacks over these years deliberately show that in cyberspace, organizations should implement a 0-trust defense model.
The main reasons for the failures of existing SOCs, mostly are the use cases of brute force login attempts, failure logins, failure HTTP requests, and malware propagations.
Nevertheless, we have to understand when the defenders started to learn, the offenders also evolved in a better way.
APT groups are evolving and abusing genuine applications we use often and stay in dwell time for years without being caught.

Advanced Persistence Threat, These groups are not an individual identity. They are mostly organizations or countries (based on agenda/political reasons) with expertise teams.
Not normal experts, they are trained professionals and they have the potential to break into any system and move laterally in a LAN without being caught for years.
Even your antivirus cannot detect this movement, because they do not create malware, it just abuses genuine applications (like PowerShell) and moves laterally like a genuine process.
Key components of an APT are, moving laterally, being persistent, creating a CnC channel, getting payload with just a DNS request, and more.
Every APT attack so far recorded, they do have unique ways of propagating a network and they rely highly on open ports, unprotected network zones, vulnerable applications, network shares, etc.
Once they break in, they do whatever they intend to do.
Your perception towards the defense against any modern-day cyber-attacks and APT attacks, you should think and build a defense mechanism exactly like an “adversary“.
For building a defense model, you should know the adversary tactics, and how they get in. How do they propagate? How do they exfiltrate?
For these queries, Lock Martin’s cyber kills chain and Mitre ATT&CK give a better understanding of the attacks. Exactly how an adversary sneaks into your network and how he moves out without being caught.
You can also, implement use cases in your existing SOC based upon the stages of the Cyber Kill chain, which will provide you an insight into the cyber-attacks.

Blocking the IOCs and IPs does not provide you 100% security over cyber-attacks.
Recent APT attacks are evolving much, using DGA algorithms and often changing domains, source IP addresses using VPN and TOR nodes (DarkNet), spoofing, etc.
As per the record, so far 5 million IP addresses have been blacklisted globally because of malware attacks, cyber espionage, APT, TOR, etc.
Let us assume our existing SOC; are we going to put watchlists for monitoring 5 million blacklisted IPS in SIEM? On the other hand, are we going to block the 5 million blacklisted Ips in perimeter firewalls?
Both were considered as plans of action, not as incident responses.
APT groups are using various techniques and hiding their traces forever, so just depending on IOCs (IP, domain, hashes, URLs) does not work anymore.
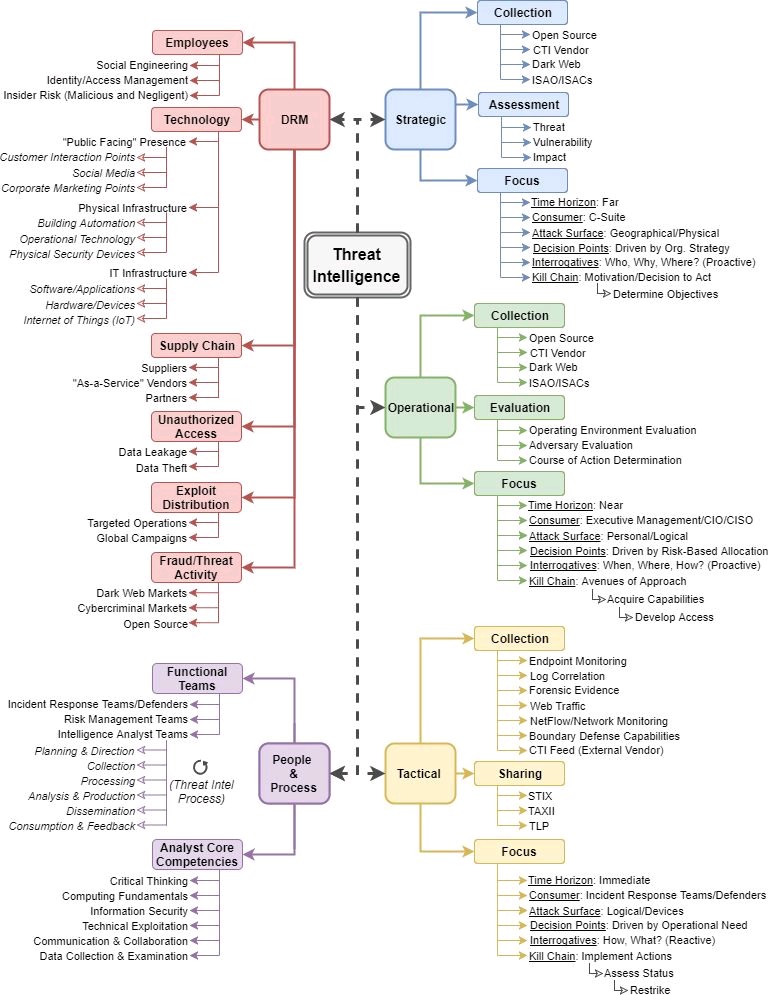
You should think about TTPs (Tactics, Techniques, and Procedures also sometimes referred to as Tools, Techniques, and Procedures).
These TTPs play a vital role in gathering information about the OS and network artifacts used by the adversaries, Based upon the information, building a use case for cases in a specific way of traffic or specific “dll” or “exe”, provides insight over the attacks.
DarkNet intelligence is also needed, where most of the stolen data are sold in the dark market for money or further asylum.
Threat intelligence also provides global threat information based on available resources. Many OEMs are also providing various threat matrix information, tools used, artifacts used, etc.
Every day, your intelligence team should gather information not only about IOC’s also; they have to strive for details about emerging IOAs and IOEs.
APT groups are well-trained in exploiting the vulnerability.
Therefore, we need to gather more information for the indications of exploitations in the organizations and ensure it is fixed before the adversary exploits.
A cyber intelligence program is all about uncovering the who, what, where, when, why, and how behind a cyberattack.
Tactical and operational intelligence can help identify what and how of an attack, and sometimes the where and when.
After figuring out what we need to know, we have to go hunting. Cyber threat hunting is a current way to learn about cyber kill chains or Mitre attacks and find new types of attacks that haven’t been seen before.
When you know what’s going on in your LAN, you can move right into responding to an incident.
But threat hunting is used when you think something bad has happened and want to look in your LAN for signs of unknown versions (APT).
When you go threat hunting, you get a detailed look at the threat routes and can narrow down the events before they turn into an incident.
Threat-hunting teams should be hired by every organization. They look for suspicious events and make sure they don’t turn into mishaps or a breach by an enemy.
They should know about the past of APT attacks and look for signs of them in their network. Not to look for IOCs that are already known and to break down the methods they use.
Exactly what to hunt? – Examples
In the same way, there are many ways to hunt in a LAN. We can use the Mitre ATT&CK structure to look at the APT’s past and figure out what happened.
It will help us understand things better, and we can compare the ways we hunt to the framework to see how far we can get.
Dwell time is the amount of time that an attacker stays in your network and learns about every zone, share, database, network protocol, mapping, route, vulnerable target, etc.
Threat hunting helps you figure out how cyberattacks move laterally and how they keep happening.

The traditional incident reaction involves figuring out what went wrong and fixing it. Threat hunting, on the other hand, involves looking for strange or suspicious events and fixing them before they become an incident.
However, any SOC needs an incident responder and a response team. These people help to stop the current incident from getting worse and fix any open security holes. This breaks the attack chain and makes cyber threats less likely.
The IR team should make sure that the CIA wasn’t broken into and that no data was taken. The cyber kill chain model can also be used by incident reaction teams to map out the attacks and put them in order.
An incident response plan can help a business by showing how to shorten the time and damage of a security incident, figuring out who needs to be involved, speeding up the recovery process, reducing bad press, and, in the end, boosting the confidence of corporate executives, owners, and shareholders.
As we’ve seen and experienced different APT attacks and cyber spying in the modern world, we should adapt and make a better cyber security plan.
This model gives us information about cyberattacks, so we need teams of experts with different skills.
Threat hunting, open source threat intelligence, and DarkNet intelligence. Proactive event handlers and first responders, malware researchers, and people who know how Windows works and how malware acts.
These skill sets are mostly needed to defend a network against modern-day cyber-attacks.
An example, is how a modern CyberSOC team should be planned.
Cyber resilience is a new idea that is quickly getting more attention. Information protection, business continuity, and (organizational) resilience are all a part of this idea.
The idea behind this model is to bring together Threat Intel, hunting, reaction, and SOC to give an organization a complex set of security structures.
It will be more helpful to put the actions in order of importance, and it will be easy to defend ourselves against attacks in the modern world.
“Adaptive response, Analytic monitoring, Deception, Intelligence, Diversity, Dynamic positioning, privilege restriction based on existing policies, realignment of mission-critical and noncritical services/servers, correlation of events, and rapid responses” are all important parts of this model.
It mostly talks about APT risks and gives a detailed look at the attack and possible entry points.
Remember,
Earlier: “Malware or Malicious”, was classified as scripts that intend to do something. But in the POV of an APT or adversaries, they know the current antivirus functionalities and their defensive mechanisms.
So they do not rely much on scripts or malware, instead, they abuse genuine programs and move laterally without being detected.
Cyber Threat Hunter POV – Whatever is not needed for an individual, in any endpoints, or in an organization, these vulnerable keys are the critical assets of an APT.
So these are considered malware in the perception of threat hunters.
Ex: “PowerShell is not used by everyone unless needed by admin in servers. So not disabling the execution of PowerShell in endpoints is a loophole and adversaries can exploit it.
This model has a five-point view of the deployment of each module, where “Threat Intelligence”, “Cyber hunting”, “SOC”, “Incident Response” and “kill chain models”.
These are the pillars of the CyberSOC and they can be separately maintained or used as per organizational policies. However, everything should be synchronized logically, and each module effectively when a suspicious event occurs.
1.What is SOC process?
SOC, which stands for “System on a Chip,” is the integration of multiple electronic components into a single processor.
2.What is SOC testing?
In the context of information technology and cybersecurity, SOC testing refers to “System and Organization Controls” testing.
It is a set of standards developed by the American Institute of Certified Public Accountants (AICPA) to evaluate the control of financial information for service organizations.
The testing seeks to ensure that service providers manage data securely to safeguard the organization’s interests and the privacy of its customers.
3. Is SOC compulsory?
System and Organization Controls (SOC) are not universally required. Some organizations require it for vendor selection to ensure data and system security based on their business requirements.
In certain industries, regulatory requirements may necessitate SOC reporting or its equivalent. In addition, some contracts may require SOC reporting as a prerequisite for business partnerships.
Nevertheless, many businesses implement SOC procedures voluntarily for risk management and market differentiation.
If you want to leave a comment, please log in first.
Comments